How does an RFID system work?
RFID is sometimes perceived as a “magic beep”. In reality, it’s a perfectly orchestrated chain that starts with a radio wave emitted by a reader, awakens a tag placed on an object, recovers a unique identifier and transforms this reading into a decision that can be exploited by your systems (receipt validated, pallet compliant, part passed to the station, item located). Until this transformation is mastered, RFID remains a laboratory test. When it is, you gain ultra-fast inventories, secure shipping and robust traceability.
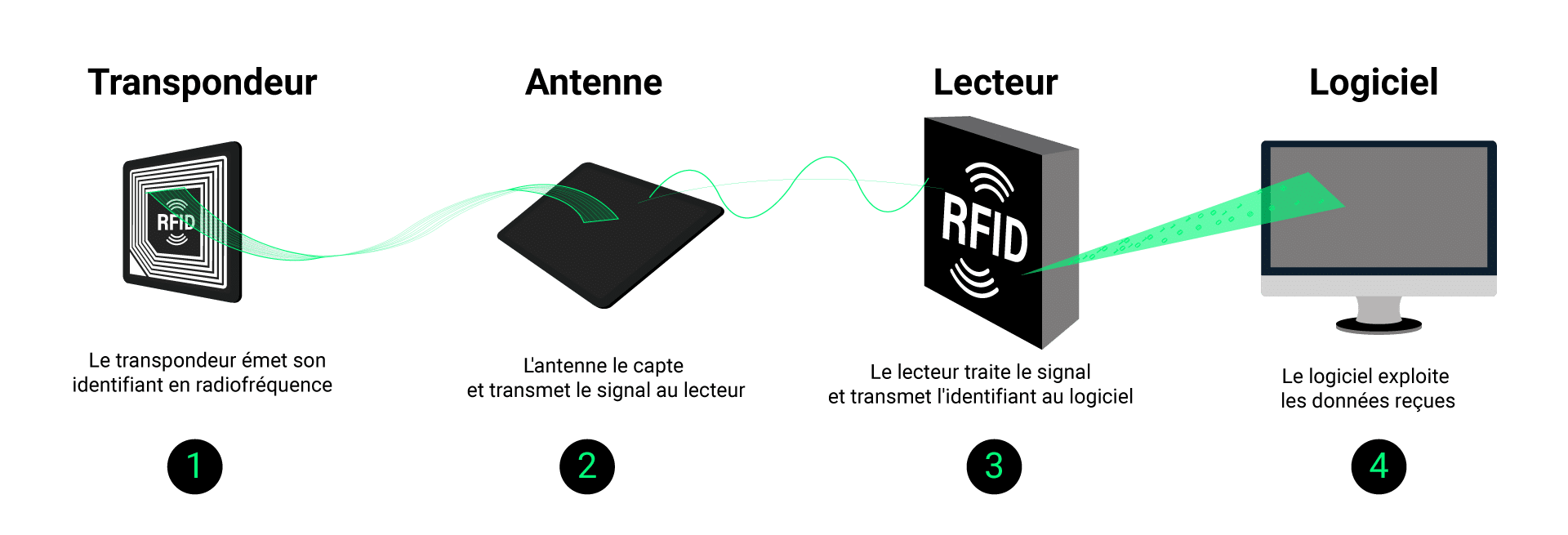
1) The three building blocks that make RFID work
An operational RFID system always relies on three building blocks: the tag, the reader/antenna and the software.
The RFID tag contains a chip and an antenna. In passive RFID, it is powered by the field emitted by the reader; in active RFID, an internal battery extends the range. The tag is attached where the value is located: on the part, bin, crate, pallet or tool. Its role is to carry a unique and reliable EPC (Electronic Product Code). The choice of tag depends on the support material (cardboard, plastic, metal, glass), the environment (heat, cold, washing, sterilization) and the desired range. For a more detailed selection, consult our RFID tags guide.
The reader creates the radio field, listens to the responses and dialogues via an anti-collision protocol to interrogate several tags present in the area. It can be fixed (gantries, tunnels, conveyors, workstations) or mobile (UHF gun for inventories). The associated antenna defines the reading bubble: angle, polarization, gain and positioning are more decisive than raw power.
RFID middleware is the orchestra conductor. It transforms a stream of sometimes redundant readings into proper business events: “pallet P123 exiting dock A at 10:32”, “parcel C456 missing”, “tooling O789 clocked in at station 3”. It filters, deduplicates, time-stamps, applies rules, then injects the event into your WMS, MES or ERP. See : RFID software solutions.
2) The reading cycle, step by step
Imagine a cardboard box passing through a shipping tunnel. As it approaches, the antennae create a reading volume. The tag picks up the energy, wakes up and sends back its identifier. Several tags respond at the same time; the UHF protocol (GS1 EPC Gen2 / ISO/IEC 18000-63) divides the dialogue into “slots” to avoid collisions. The reader then produces a list of EPCs read, with the antenna concerned and a signal level. At this stage, the data is raw.
The middleware takes over. It groups readings belonging to the same passage, deletes duplicates, applies a time window and compares the result with what is expected (list of items on the order, SSCC of the pallet, item reference). At the output, only one clear event remains: “pallet compliant” or “item missing”. The information is then transmitted to your WMS (to validate the shipment), your MES (to acknowledge the progress of an OF) or your ERP (to update a document). It’s this “physical → digital → business” translation that makes RFID so valuable.
3) Frequencies: why LF, HF/NFC and UHF don’t give the same result
Frequency determines range, reading speed and environmental sensitivity.
- LF (125-134 kHz) reads at very close range and is resistant to water and metal. Used for access control or animal identification.
- HF (13.56 MHz) includes NFC. Short to medium range, excellent for proximity interactions (cards, library, nearby rooms).
- UHF (860-960 MHz), also known as RAIN RFID, is the star of logistics and industry: mass reading at several meters, hence flash inventories and shipping tunnels.
Beyond frequency, regulations differ between zones (ETSI in Europe, FCC in America). If you operate internationally, choose equipment that is multi-region compatible. For the basics, go to RFID frequencies and standards.
4) EPC encoding and printing: the identity card for your objects
Each tag must carry a unique identifier. TheEPC provides this worldwide uniqueness, with different schemes depending on your needs: SGTIN for single serialized products, SSCC for pallets/packages, GRAI for reusable containers, GIAI for assets. In production, an RFID printer encodes the EPC in the chip and prints the label in a single pass. Failure control is essential: retry if necessary, otherwise scrap the tag and log it. On the governance side, you need to master numbering ranges, series uniqueness and the correspondence between EPC – reference – batch – order. For a detailed definition of EPC, see the RFID Technology pillar article.
5) Where performance is gained (or lost): on-site RF design
Reliable RFID isn’t achieved by pushing power to the limit. It is achieved through careful RF design:
- Antenna and polarization. In a controlled environment, linear polarization maximizes performance; otherwise, the circular antenna is more tolerant of random tag orientations.
- Contained reading zone. Too much power enlarges the bubble and creates spurious readings. Better several well-aimed antennas than one strong one.
- Difficult environments. Metal reflects, water absorbs. We use on-metal tags, create gaps (spacers), orient the reading and, if necessary, shield certain sides of the tunnel or gantry.
- Method. We test on your premises, on your media, at your speed. We measure read rates, false-positive rates, stability over time, and make adjustments.
The real objective is not record-breaking on the test bench, but repeatability in your real-life conditions.
6) Four typical operating scenarios
Shipping tunnel. Packages pass through, and the list of expected EPCs is compared with the list read. In the event of a discrepancy, an alarm is displayed and the operator corrects the situation before a dispute arises. The tunnel combines several antennas, calibrates power by zone and applies fine tolerances.
Dock gantry. At the entrance to a zone (workshop, SAS, dock), a gantry automatically detects passageways. The middleware aggregates by logistic unit (SSCC), manages the direction (entry/exit) and declares the event to the WMS.
Workstation. On a template, an antenna reads a part or batch at the key moment. If several tags respond when only one is expected, the station blocks and displays the cause. This “simple, repeatable” control is a highly effective form of quality assurance.
Mobile inventory. Using a UHF terminal, the operator scans an aisle. Mass reading enables a rotating inventory in minutes, synchronization with the WMS handles discrepancies, and a directed search locates an item by matching the power received.
These scenarios are simply variations on the same logic: read cleanly, filter intelligently, decide clearly.

7) From reader to IS: the pivotal role of middleware
Without middleware, your systems would receive a barrage of unreadable readings. Middleware applies time windows, removes duplicates, adds context (site, station, antenna, operator) and transforms the reading into a business event. It then exposes secure APIs, feeds event queues or generates files according to what WMS, MES and ERP consume. The criteria that count: low latency, standard connectors, observability (logs, metrics), ease of administration and network security.
For the division of roles between WMS/ERP/MES, please refer to the dedicated section in the RFID Technology pillar.
8) Safety, compliance and best practices
RFID mainly manipulates object identifiers, but it’s an integral part of your IT/OT policy. Exchanges must be encrypted, services authenticated and networks segmented. On the tag side, we activate access protection (read/write) and document deactivation policies ( kill command as appropriate). If personal data is correlated (e.g. nominative PPE), privacy by design, purpose limitation and logging are applied. In short: RFID can be integrated into the security standards you already apply to your industrial applications.
9) How to deploy: a realistic, measured trajectory
Successful RFID deployment involves four steps.
- Framing. We map the flow, position the reading points, define the target KPIs (reading rate, inventory time, disputes) and integrate the system.
- On-site POC. We compare several tags, adjust antennas and power, and check the stability of readings.
- Pilot. We switch over a significant area, train the operators, refine the rules in the middleware and measure the real impact.
- Industrialization. We standardize the EPC, templates, connectors and supervision, then duplicate.
For sector-specific inspiration, see RFID in industry.
Faq
Our answers to the questions often asked by our customers
In UHF, yes, that’s precisely the point: reading without line-of-sight and en masse, for example in a shipping tunnel.
The reading bubble is undoubtedly too large or badly oriented. We reduce power, reorient antennas, shield if necessary, and reinforce filters on the middleware side.
In most projects, yes. Encoding EPCs governed by your IS ensures uniqueness and interoperability (SGTIN for products, SSCC for pallets, GRAI for bins, etc.).
Not always. The two often coexist: barcode for occasional unit readings, RFID for mass controls, flash inventories and areas with no line of sight.
UHF for remote and mass reading in logistics/industry. HF/NFC for proximity scanning with operator or smartphone interaction. See : RFID frequencies and standards.